PortX Integration Manager Architectural Overview
Introduction
Purpose
This document provides an overview of the PortX Platform including brief descriptions of the tools provided to develop, build, and stage applications, and to deploy and host production applications.
Initialisms
| Initialism | Definition |
|---|---|
| API | Application Programming Interface |
| AWS | Amazon Web Services |
| CD | Continuous Delivery |
| ECR | Elastic Container Registry |
| MFA | Multi-Factor Authentication |
| RDS | Relational Database Service |
| VPS | Virtual Private Cloud |
| VPN | Virtual Private Network |
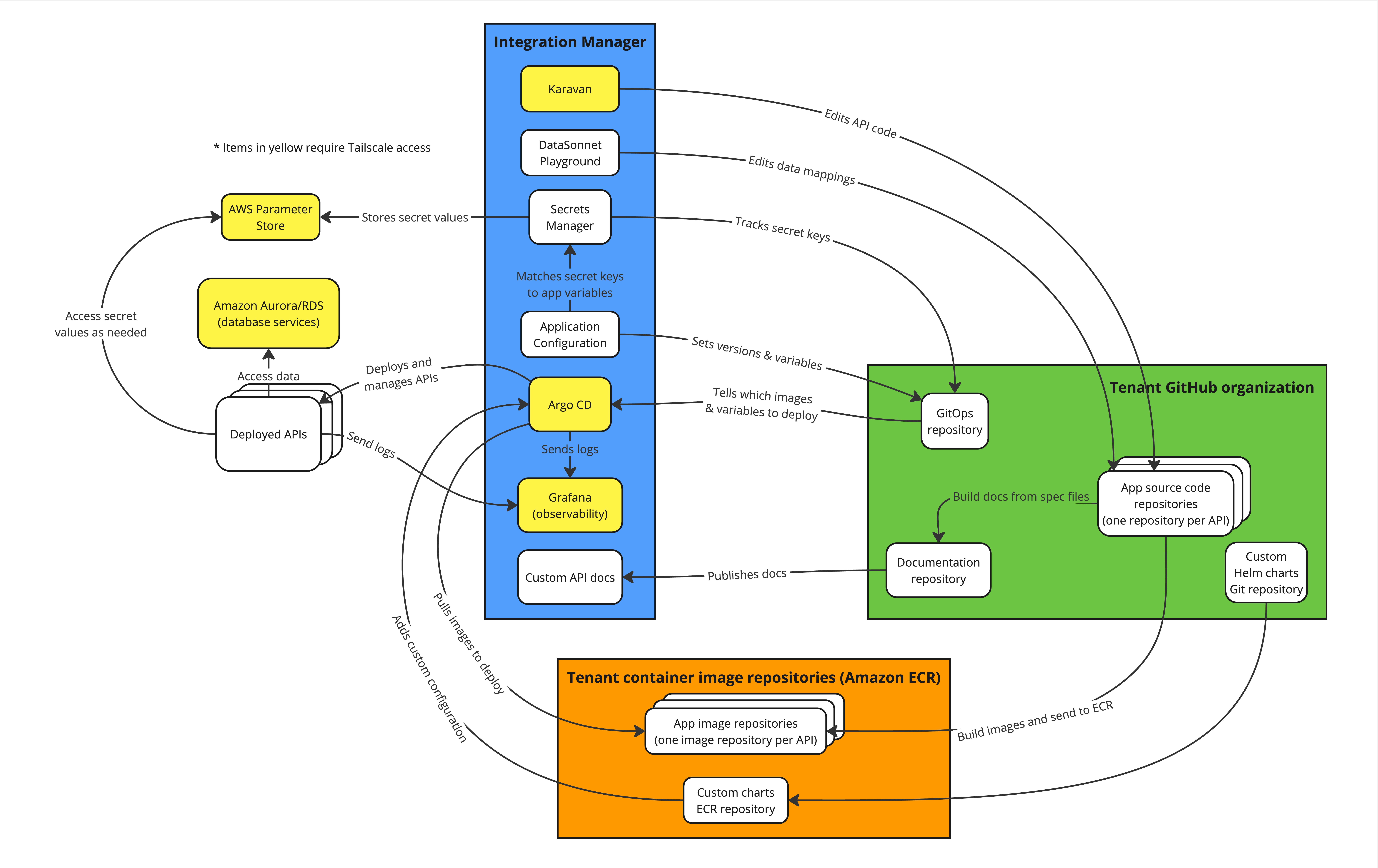
Overview
The PortX Platform provides a set of robust tools to enable companies in the financial services industry to develop, build, and stage applications, and to efficiently deploy and host resilient production applications.
Figure 1 shows the customer-accessible resources of the PortX Platform and how those resources interact enabling developers to develop, build, deploy, observe their applications in pre-production and production environments.
Authentication and Authorization
Authentication
The PortX Identity and Access Management manages authentication when you log onto the platform by performing strong identity establishment, including MFA on signup, and identity verification upon login.
Authorization
The PortX Identity and Access Management is the central authority for permissions and access to everything the platform provides.
Integration Manager
The Integration Manager is a central hub for the API-centered features of the platform.
The Integration Manager includes the following components:
- Your custom API Catalog
- DataSonnet Playground
- Karavan development space
- API and API Gateway
- Visibility and controls for the following features:
- GitOps deployments
- API metrics, logs, traces, and alerting
Source Control Repositories
The PortX Platform uses GitHub to manage source control for code, configuration, and deployment.
Tenant Repositories
For every new tenant account, the PortX Platform creates a GitHub organization and provisions the following 3 tenant repositories.
GitOps Repository
The PortX Platform uses declarative GitOps for deploying applications to both pre-production and production clusters. In the repository, application Helm charts and values configuration files are committed for Argo CD to perform the specified deployment. Argo CD deploys the specified application in the cluster/environment corresponding to one of the following selected branches:
- Development (dev)
- Staging (stg)
- Production (prod)
Charts Source Repository
In addition to a centralized repository of generic pre-built Helm charts, the PortX Platform provides a custom repository for each tenant to create their own Helm charts for application deployment.
Documentation Repository
For each tenant, GitHub org includes a documentation repository which is configured to automatically generate and publish documentation for the tenant’s custom APIs. Workflows in the repository pull OpenAPI spec files from each application source repository, and build a compiled documentation site using Docusaurus. The site is accessible in the Adopt module of Integration Manager.
Application Source Repositories
Each API has its own application source repository.
When you create a new API from the Integration Manager’s API Catalog, you can select from several API templates. The PortX Platform then provisions an application source repository for storing the API source code. The repository includes starter template files and automated workflows for building and deploying the API.
Container Repositories
The PortX Platform manages repositories in Amazon Elastic Container Registry (ECR) to store either Helm charts or application images for reference in GitOps deployment.
Tenant Charts Package Repository
If you create a custom Helm chart in the charts source repository on GitHub, the packaged chart is stored in the tenant charts package repository on ECR.
Application Image Repository
In addition to an application source repository, each API has its own application image repository. Application images built from the source repository are pushed to the application image repository to be referenced for GitOps deployment.
TailScale Accessible Resources
Tailscale provides site-to-site networking and performs as a type of VPN to provide AWS VPC access to resources and applications stored inside your private AWS account.
Cluster Administration and Monitoring
Direct cluster access is restricted. Instead, PortX Integration Manager provides embedded interfaces for API cluster administration and monitoring using the industry-leading tools of Argo CD and Grafana.
Argo CD
Argo CD enables the following activities:
Developers can see the status of their application deployment in both pre-production and production environments.
The live-tailing of logs in the pod in which an application is running. The tail command provides the ability to stream the most recent logs in real-time.
Developers can access a pod’s shell or terminal to troubleshoot in the application’s runtime environment.
Grafana
Grafana provides access to the centralized logging facilities of the PortX Platform.
In the centralized logging facility, you can perform the following activities:
- Configure alerts
- Search application logs
- Perform distributed tracing to profile and troubleshoot API calls
Karavan
Karavan is a low-code visual tool for building and connecting APIs. Karavan includes a built-in development environment for testing API calls as you work. Because this environment runs in the app cluster, Karavan access requires Tailscale.
AWS Services
The PortX platform provides direct, Tailscale-protected access to select AWS services for supporting your APIs in both pre-production and production clusters.
Databases (Relational Database Services)
When connected with Tailscale, developers can utilize a database’s private endpoint to use thick clients to aid in query development or troubleshooting.
Parameter Store
Secrets are stored in AWS Parameter Store and pulled into a cluster through the External Secrets Operator. You can create, update, and delete secrets using the Secrets Manager interface in Integration Manager, which tracks key names in GitOps and stores the values in Parameter Store. In rare instances, when direct Parameter Store access is needed, connect with Tailscale for the direct access.